Building a Cybersecurity Strategy: Vulnerability Management
Prioritization of Vulnerabilities
In this blog post that continues the ‘Building a Cybersecurity Strategy’ series, we aim to cover Vulnerability Management.
Effectively running a vulnerability management program can be extremely challenging as there are so many flaws and vulnerabilities released every day. It is imperative to have a plan in place so that vulnerabilities can be identified, prioritized, and remediated in an effective manner.
What is a Vulnerability?
A vulnerability is a flaw in a system that can allow for adversarial exploit resulting in misuse ultimately threatening confidentiality, integrity, and / or availability of an asset. Less technically speaking, a vulnerability is a hole in security that an attacker can leverage to misuse a system in an unauthorized manner.
There is a wide variety when it comes to the types of vulnerabilities disclosed. The severity of vulnerabilities can be determined by factors such as how easy they are to exploit, the impact of a successful exploit, and whether or not an exploit is actively available. With so many different types, it is important to leverage tools to help identify vulnerabilities within the organization.
Scanning for Vulnerabilities
Scanning for vulnerabilities can be accomplished by numerous commercial and open source tools. Regardless of the solution accepted by the organization, management should ensure that all systems are being scanned by the tool in order to identify relevant vulnerabilities.
Consideration should be taken regarding which tools are selected as some tools specialize in internal vulnerabilities & configurations while other tools specialize in publicly facing web applications. As scans are performed, the organization will be presented with a catalog of vulnerabilities including impacted assets and the severity of said vulnerability.
With a list of vulnerabilities, the organization must prioritize the remediation of vulnerabilities and establish the urgency around how quickly remediation must occur.
Understanding CVSS
The ‘Common Vulnerability Scoring System’ (CVSS) was developed to standardize the severity of any given vulnerability as they are announced. It allows the opportunity for organizations to prioritize vulnerabilities as they’re announced based on the 0 to 10 score.
At a basic level, a 10.0 is very very bad while a 1.0 is relatively benign. There are several elements that go into the calculation of the score that can be explored using the NIST Vulnerability Scoring System Calculator.
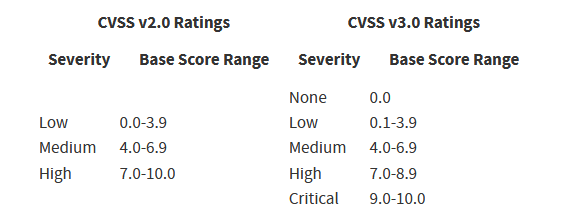
It is important to note there has been several iterations of the CVSS, and it is currently on version 3.1. NIST has released a comparison between version 2 and 3 can be found below:
The NVD added the ‘None’ and ‘Critical’ fields in the iteration from 2.0 to 3.0.
With an understanding of CVSS, a plan can be put together within an organization as to how to respond to vulnerabilities and general patch management. CVSS is very helpful in terms of prioritizing, but some additional fine turning can allow for a more refined strategy.
Prioritizing Vulnerabilities in an Organization
There is a caveat to CVSS, and that is that it can be dangerous to take a score at face value without exploring the impact of the vulnerability specific to the organization.
For example, consider a CVSS score of 9.5 and 7.5. Say the 9.5 vulnerability exists within a server internal to the organization while the 7.5 exists in a publicly facing web applications. While the ‘Critical’ is quite concerning, it is more important to remediate the 7.5 due to the fact that it is accessible from the internet. The 9.5 vulnerability should definitely be remediated, but when attempting to prioritize issues, anything should facing will always come first - especially if the vulnerability is actively being exploited.
Generally speaking, the following approach can be taken in terms of establishing priority in which vulnerabilities are addressed:
Any ‘Critical’ or ‘High’ vulnerabilities publicly facing & actively exploited.
‘Critical’ vulnerabilities publicly facing.
‘High’ vulnerabilities that are publicly facing.
‘Critical’ vulnerabilities internally facing with active exploits.
‘High’ vulnerabilities internally facing with active exploits.
‘Medium’ vulnerabilities publicly facing with active exploits.
‘Critical’ & ‘High’ vulnerabilities internally facing.
‘Medium’ & ‘Low’ vulnerabilities externally facing with active exploits.
All other ‘Medium’ and ‘Low’ vulnerabilities internal and external.
Note: This is a rough guide to follow; organizations may need to tweak the above depending on what patching capabilities are within the organization.
Extra Considerations & Priorities
It is highly recommended to consider the ‘Known Exploited Vulnerabilities Catalog’ maintained by the Cybersecurity & Infrastructure Security Agency. The list consists of vulnerabilities the agency has actively seen criminals leverage in cyber attacks. It is highly recommended to place these vulnerabilities as a top priority within the vulnerability management program.
Another resource is the ‘Top Routinely Exploited Vulnerabilities’ released by CISA. Again, it is highly recommended to prioritize these issues as exploitation often leads to unauthorized access, theft, and even ransomware.
Conclusion
Developing an effective vulnerability management program can be challenging. It can be daunting to select a vulnerability scanner, prioritize identified vulnerabilities, and effectively patch and remediate vulnerabilities. For further assistance on establishing the programming and exploring optimizations such as metrics and service level agreements, do not do it alone.
Reach out to Thoreson Consulting for help!