How to Gut a Phish [Dissecting a Phishing Email]
We Caught a Phish!
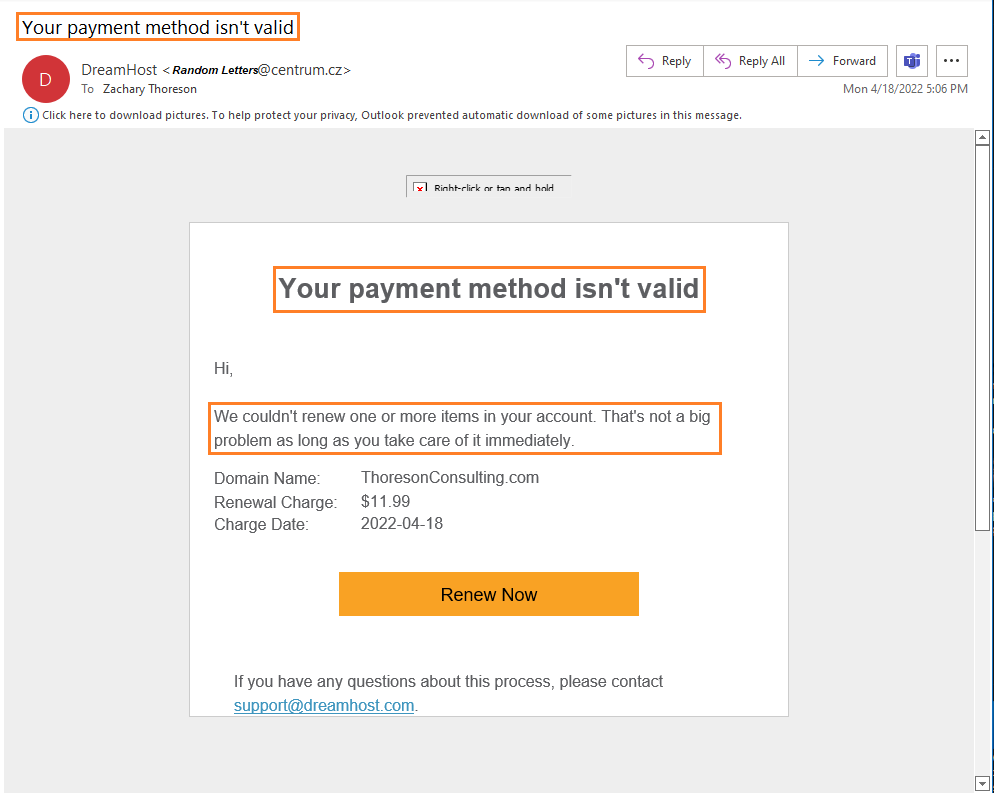
I received a phishing email today informing me that the ThoresonConsulting.com domain could not be renewed. The email stated that this is not an issue provided I fix the billing issue immediately and offered a seemingly convenient button to take me directly to the page to fix the problem. Like one of millions that others receive every day, I had encountered a phishing email.
Thoreson Consulting assists its customers in incident response and has seen numerous phishing campaigns over the years. It is common to see the same type tactics to grab attention, establish credibility, and redirect phishing victims to the payload - generally resulting in stolen credentials or the distribution of malware.
When reviewing a phishing email, look for the following:
A Call To Urgency
Spoofed Senders
Illegitimate Links
Let’s take this opportunity to review what gave away this malicious email as a phish.
Note: All indicators of compromise have been removed for the safety of the audience.
Inspecting a real phishing email
On Monday, April 18th, 2022, Thoreson Consulting received the following email:
An email Thoreson Consulting received claiming its purchased domain had expired
When first reading the email, the content of the email is concerning. It is informing me that my payment information is not valid and that if I don’t take care of it quickly, there could be issues renewing my domain. Obviously I don’t want to lose the ThoresonConsulting domain and the email is targeting that concern.
But - as the title of the blog post has revealed - this is a phishing email.
Outside of the fact that ThoresonConsulting.com is not hosted by DreamHost, lets dig into this message to understand how we know this is a phishing email.
Call to urgency
Phishing emails will often urge the victim to act quickly. In this case (highlighted in orange below), the phishing email is attempting to generate urgency by stating the payment for the domain is invalid. The attacker wants me to think ‘as long as I act quickly, it is not a big problem’ and provides a button for me to click on.
Often times the emails will be very short and to the point with a button, link, or file attachment for the user to click on. The attacker is hoping that there is not much thought put into the legitimacy of the email before clicking the giant orange button.
The language used in the phishing email preys on the human response to urgency
Attackers will often use headlines and content that raise concern in their intended audience. This can be anything from claims of embarrassing photos or information on an individual to phishing emails urging action regarding ongoing business.
Common phishing campaigns include:
Embarrassing photos of an employee
Updated contracts, proposals, and business documents that require review
Spoofed emails from the CEO urgently requesting an employee assist them
Expiring passwords, accounts to be deleted, login information not valid, email addresses set to expire
Tax season and related topics -> W2 information not valid, confirming addresses, refund not valid or stolen
Bonuses, promotions, prizes (tickets, gas cards, free parking)
Beware Spear Phishing
In addition to the common campaigns, keep in mind there also exists highly targeted phishing campaigns known as ‘spear phishing’ campaigns where the attacker attempts to custom tailor the phishing email to the victim. An example includes emails appearing from prestigious universities or conferences requesting executives or researchers to speak at their event. The attacker aims to get access to organizational accounts with more sensitive information.
Keep an eye out for these type of emails. If it is too good to be true or extremely concerning, always stop and reconsider all of the circumstances. The best solution is to get a second opinion from a manager or the IT / Security team.
Investigating the spoofed sender
Often times, the ‘Sender Name’ will not reflect the actual sender’s address - a technique known as ‘Masquerading’ or more commonly called ‘spoofing’. In this case (seen in orange), the email’s Sender Name was ‘DreamHost’ however the email itself was sent by an address containing a mix of letters and numbers from the @centrum.cz.
A quick google search of the centrum.cz domain reveals that this is not related to DreamHost but rather a personal email service based out of the Czech Republic:
A quick google search reveals the domain belongs to a personal email service
Attackers often spoof the sender’s address to build trust from the victim. CEOs, Managers, and trusted vendors are often spoofed to build trust or authority as the victim reviews the email. Validating that the ‘Sender Name’ and ‘Sender Address’ match is often a quick way to rule out whether an email is legitimate.
Illegitimate link
Hovering over the ‘Renew Now’ button, we find that the button takes us to a different website than where ‘DreamHost’ should be (seen below). This is the payload - often attackers will have this website attempt to download files, appear to be a fake login screen to capture credentials, or other nefarious actions.
Hover over the link to see its redirection
Investigating the link
Note: It is not recommended to interact with potentially malicious emails. If you’re uncertain, the best course of action is to report it as spam and let your security team take if from there.
Taking this a step further, we can leverage UrlScan.io to check the link.
As seen in the screenshot below, the url takes us to a website pretending to appear as the DreamHost portal. This is likely attempting to gain access to user credentials in order to take over domain / web hosting services.
URL Scan Result:
Google Safe Scan = Malicious
Screenshot - Shows Spoofed Website Portal
The website preview shows a spoofed login page targeting DreamHost customers
Fighting Back
Analysts often use these techniques to grab indicators such as the various URLs used by the attacker, the hosting company, and the email address to block the attacker from reaching additional victims. Additionally, such evidence can be collected and shared with hosting websites and email providers to ban and remove malicious content from the internet.
Wrapping up
Don’t believe everything you see.
When slowing down and reviewing the context of the e-mail, it becomes easy to spot this real world phishing attempt. It is important that even if you do fall for such a scam, you alert your IT staff and immediately change your password.
Securing your users
So many security breaches start with a compromised user account. To learn more about securing user accounts, check out our blog on ‘Building a Cybersecurity Strategy: Identity Access Management’.
Contact Thoreson Consulting to learn more about security awareness training. We can assist you in training users to spot similar emails as well as the importance of data privacy and security best practices.