Use a Risk Assessment to Kick off a Robust Information Security Program in 5 Easy Steps
There are a variety of ways organizations can take steps to reduce the chance of a cyber incident from occurring. An Information Security Program (ISP) contains the physical, technical, and administrative objectives in place by an organization to keep the its customers, employees, and assets safe. Whether it is seeking to prevent a data leak or concerns about ransomware, it is imperative to establish an ISP.
One of the first things an organization can do when attempting to come up with a strategy, is leverage a Risk Assessment to establish a security baseline of the organization. In doing so, the organization can identify what it is doing well and where its gaps in security may reside.
What is a ‘Risk Assessment’
According to the National Institute of Standards and Technology, a risk assessment is defined as:
The process of identifying risks to organizational operations (including mission, functions, image, reputation), organizational assets, individuals, other organizations, and the Nation, resulting from the operation of an information system.
Through a risk assessment, organizations can identify the gaps in their ISP that could result in risks to the organization to be realized. This can lead to loss of sensitive data, legal or financial penalties, or even cyberattacks.
Organizations seeking to implement or improve an existing ISP should first begin with a risk assessment to establish a baseline. A successful risk assessment will result in a report that documents all identified risks to the organization. From here, the organization can begin to strategize on how it can tackle these risks to improve its cybersecurity posture.
Thoreson Consulting leverages a checklist of administrative, physical, and technical objectives organizations should accomplish, known as controls, to assess how at risk an organization to the realization of its vulnerabilities.
Strategy: From Risk Assessment to ISP
With a completed risk assessment in hand, organizations can then begin to build and fill-in the gaps of their ISP. The general strategy is as follows:
Scope and Complete a risk assessment
Remediate highest severity identified risks to the organization
Remediate issues identified as ‘Quick Wins’
Prioritize and assign remaining risk items in a ‘Risk Register’
Establish and Update ISP Documentation
We will explore in this blog post each of the above outlined steps to better understand the process and provide guidance in establishing the first steps on an organization’s journey to a complete ISP.
Scope and complete a risk assessment
As outlined above, a risk assessment contains a grouping of controls to assess the overall effectiveness of the objectives taken to reduce risk to the organization. A key part of completing a risk assessment is determining the scope of the assessment.
There are a number of topics that make up an ISP grouped together in whats called a domain. The domains included in a risk assessment vary depending on which framework is being applied, but generally aim to group the controls by a common theme.
It is up to the organization and the consultant to agree on which domains and their underlying controls make sense to be included in the risk assessment. This should be clearly defined in the scope and detailed in the full report. Failure to properly scope a risk assessment may result in missed risks to the organization increasing the chances of an incident occurring.
Example: Social Media Marketing Company
An organization with remote employees might have very little concern over physical security and not wish to spend time reviewing that domain. This scope can be excluded.
That same social media company can have considerable impact and brand damage should a user account become compromised giving an adversary access to the organization’s social media accounts. It is vital Identity & Access Management (IAM) is included in the scope of the assessment.
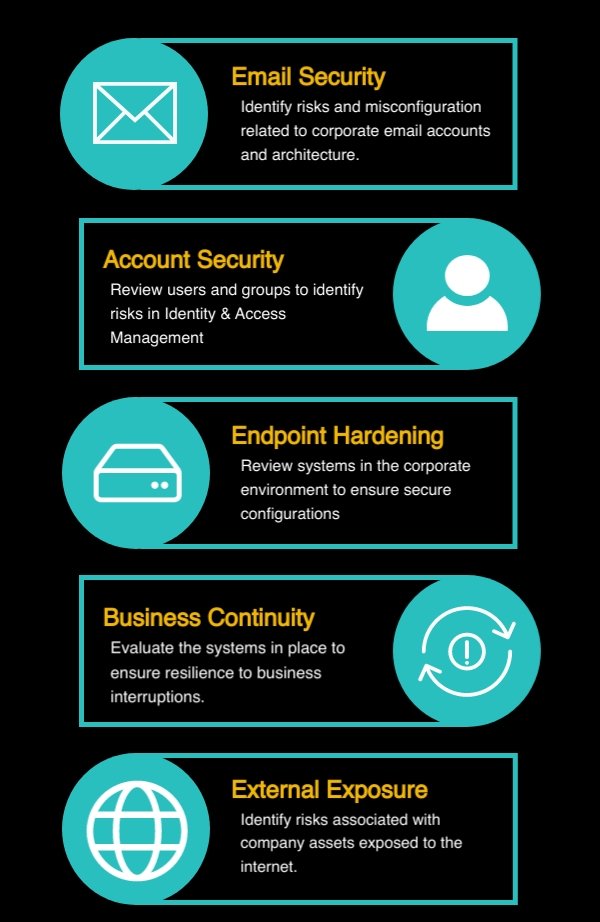
Thoreson Consulting has grouped its controls into five (5) domains that it believes most small to medium sized organizations should consider when working to implement or improve a cybersecurity program:
Thoreson Consulting includes five (5) domains in its Small Business Risk Assessment framework. These aim to review key areas that matter to small organizations without committing to a large, overwhelming framework.
Remediate highest severity identified risks to the organization
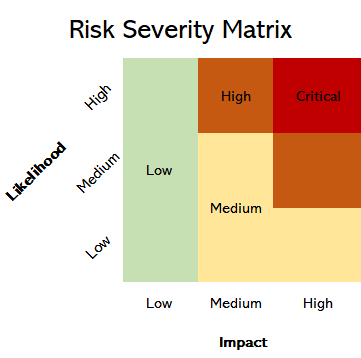
Following the completion of a risk assessment, the organization can begin to process the findings of the report. The report should include a scale of severity assigned to each identified risk ranging from ‘Low’ to ‘Critical’.
When determining the risk of any given control, the consultant takes into account the Likelihood; the chance of the risk occurring, and the Impact; the effect on the organization should the risk occur. An matrix can be built to better visualize what this may look like:
As ‘Likelihood’ and ‘Impact’ increase, the effect on the organization becomes more catastrophic.
It is highly recommended to review the critical findings of the report and immediately devote resources to the resolution of the identified critical risks to the organization.
Failure to respond to the critical issues identified in a risk assessment can put the organization in danger of the identified risks being realized. Most consulting firms performing risk assessments reserve ‘Critical’ finding ratings for only the most severe identified risks and they should not be taken lightly.
Once the most critical risks have been addressed, the organization to look towards processing the ‘Quick Wins’.
Remediate issues identified as ‘Quick Wins’
In addition to ‘Likelihood’ and ‘Impact’, there are several other attributes of identified risks in the report. Time and cost of efforts are also important components to factor into remediation planning.
Some identified risks may require the overhaul of policies and procedures, the procurement of new software, or take considerable resources away from the organization. These more intensive risks should be remediated, but the organization should first look for any ‘Quick Wins’.
Thoreson Consulting defines quick wins as risks to the organization that can be remediated with minimal cost or complexity but remove ‘high’ severity findings. By efficiently working through ‘Quick Wins’, an organization can drastically improve its security posture without consuming a large amount of resources.
We have defined a list of commonly encountered risks that can be quickly mitigated to improve cybersecurity posture. You can read more about it in our blog post: “5 ‘Quick Wins’ Small Businesses Can Take To Massively Improve Security”.
At this point, the organization should be rid of any ‘Critical’ findings and found improvement through ‘. Quick Wins’. It can then look to prioritize the remaining issues in the report.
Prioritize and assign remaining risk items
With the ‘Critical’ issues and ‘Quick Wins’ addressed, organizations will find them selves with a large number of ‘low’, ‘medium’, and ‘high’ risks remaining. Organizations should adopt the use of a ‘Risk Register’ to catalog ongoing efforts to remediate identified risks.
An effective risk register should catalog all of the identified risks to the organization while providing information on remediation efforts. An ideal risk register should include, but not be limited to, the following fields :
Identified risks including their associated likelihood, impact, cost, and complexity of remediation
Assigned employee(s) who will work to remediate the risk
Due dates or deadlines as to when the risk will be remediated by
Notes as to whether additional testing must be performed to validate risk remediation
While at first glance it may make sense to go in order of the risks by their associated risk score, rarely is that the case. Some risks may require significant resources, both time and cost, to remediate. Additionally, some risk items may be bundled or co-dependent on each other.
Example: Insecure VPN
Several risks related to an insecure virtual private network (VPN), i.e. Lack of MFA, Active Directory Synchronization, may not be able to be remediated if the current implementation is out of date and not supporting modern features. While remediation of the VPN issues may require considerable resources, it resolve several items and reduce a significant amount of risk. As such, it should be prioritized higher than working through individual risks to the VPN.
The consultant and the participating organization should strategize which risks make sense to prioritize and establish an effective order to remediate risks taking into account dependencies, legacy systems, and impact to the organization.
Establish and update ISP documentation
Organizations should consider the following as a core principle regarding documentation of their ISP:
Only document the standards, policies, and procedures the organization is adhering to and able to provide evidence for.
AKA - Do not say you’re doing something unless you’re actually doing it.
It is important, from an audit perspective, that documentation around an ISP is reflective of what is taking place at that organization with evidence to support it.
This includes ongoing but not yet complete initiatives - the documentation should come last after the policies, procedures, and standards are reviewed to reflect the organizations’ active implementations.
If an organization says they’re encrypting all their assets, they need to be able to provide evidence that they’re doing so. While documentation is important, do not produce documentation for security practices you’re not yet doing. Establish the control first, then document how it is being done.
That being said, remediating risk items discovered by an assessment is a great opportunity to evaluate and update any related documentation. As an organization works through the identified items, they should document the related control area.
Example: Documenting New Controls
An organization implementing stronger user account security, i.e. MFA, strong password policies, split administrative accounts; should document those controls in their Identity and Access Management policy. Any new accounts should adhere to this policy and the organization should be able to provide evidence of these controls.
Overall, a ISP should have documented the efforts via policies, procedures, and standards. This documentation serves as a means to a repeatable process to keep the organization secure. From a high level, a risk assessment should include gaps in documentation, but this blog post only covers the basics of governance, risk, and compliance.
Wrapping Up
The completion of a risk assessment nets an organization a large amount of information that it can leverage to begin making improvements in security posture. The steps taken to remediate the risks identified in the report can be quickly be turned into the genesis of an ISP.
It should also be noted that security is a process, not a one time effort.
Organizations should seek to complete risk assessments every few years or even annually if large amounts of progress are made against the risk register. This keeps the risk register fresh and up to date and allows for validation of the remediation efforts.
Thoreson Consulting offers a unique risk assessment for small to medium size organizations. We select a curated list of controls from several large frameworks to bring a scalable approach appropriate to small to medium size organizations. Our assessments offer a great opportunity to organizations just starting on their security journey or who have never performed such an assessment.
Contact us today for a free consultation or to learn more about our risk assessments. Also, check out our services page to see the number of other ways Thoreson Consulting can assist your organization.