5 ‘Quick Wins’ Small Business Can Achieve to Massively Improve Security
‘Quick Wins’ Provide an Impact
Thoreson Consulting works with a variety of small and medium businesses in various industries looking to improve their cybersecurity programs. While performing risk assessments and general consulting work, we often find and highlight opportunities for ‘Quick Wins’ to improve cybersecurity.
Quick Wins are easy adjustments or configuration changes, often without purchasing additional software or licenses, that can pay dividends in reducing cybersecurity risk to an organization.
Here are 5 common ‘Quick Wins’ small businesses can achieve to massively improve their security and reduce the likelihood of a cyber incident:
Enable MFA
Secure Email Authentication
Add External Sender Banners
Build an Inventory
Train Your Employees
While there is no magic bullet in cybersecurity, these 5 adjustments can often provide a high amount of value compared to their cost of implementation. If the guides included in this blog post are more technical than what you feel comfortable with, do not hesitate to reach out to Thoreson Consulting for assistance.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication, commonly abbreviated as MFA or 2FA, is critical in preventing unauthorized access to company resources. It adds an additional requirement when logging into an account to validate the identity of the user.
Consider a phishing attack where an employee is tricked into logging into a malicious website where their email and password are captured. Without MFA, an attacker can quickly leverage the stolen credentials to access resources the employee has access too such as Mailboxes, VPNs, FileShares etc.
Should that same employee have MFA enabled, an attacker leveraging the stolen credentials will have to enter an additional ‘factor’ such as a pin, passphrase, or push notification sent to the employee’s phone or token. Since they do not posses the employee’s phone, they cannot get into the account.
MFA can reduce the impact of compromised credentials. Even with a username and password, the attacker does not have access to the 2FA key resulting in a failed login attempt.
MFA is not a perfect response to phishing attacks and there are creative ways to circumnavigate MFA security. As such, it is still important to educate employees of these types of attacks as an organization cannot rely on technical controls alone to mitigate risk. See ‘Train Your Employee’s’ below, as it outlines how education reduces the likelihood of stolen credentials leading to unauthorized access into the organization.
Thoreson Consulting considers setting up MFA as a Quick Win because most modern email and collaboration software includes MFA at no extra cost. Google and Microsoft both include MFA security in their Workspace and Microsoft 365 platforms and it is becoming increasingly common for software-as-a-service (SaaS) solutions to include some form of native MFA in their software.
Both Google and Microsoft include guidance on leveraging MFA in their documentation pages:
Deploy 2-Step Verification (Google)
Set up multifactor authentication for Microsoft 365 (Microsoft)
Enabling MFA can greatly reduce the impact of stolen credentials and reduce the likelihood of unauthorized access to company information and systems. It is an essential component in a strong Identity and Access Management (IAM) strategy to keep user accounts secure. For more information on IAM best practices, check out our blog post ‘Building a Cybersecurity Strategy: Identity and Access Management’
2. Secure Email Authentication
SPF, DKIM, and DMARC can reduce the amount of junk emails inbound to an organization.
SPF, DKIM, and DMARC are three email authentication methods that, when not utilized properly, can allow an attacker to impersonate or piggy-back off email systems to target employees. It also allows for email from questionable sources to make it to employee mailboxes resulting in an increase in spam and spoofed email.
Correctly configuring these authentication methods is a quick win for the organization as it’s quick and cheap to do, but has a major impact on reducing the amount of spam and phishing emails an organization receives.
SPF, DKIM, and DMARC can be configured by updating domain name system (DNS) records and configured alongside email services to help secure email communications.
What is SPF?
Sender Policy Framework (SPF) is a way for a domain to list all of its valid IP addresses that send email from the organization. It serves as a fact check for recipients of its emails to validate that emails that claim to originate from the domain actually have done so.
Correctly configuring SPF can significantly reduce an attacker’s ability to spoof emails to appear to originate from your domain. This can cut down on spam and prevent attackers from impersonating individuals from your domain.
More information on defining SPF records can be found in Google and Microsoft’s documentation sites.
Define your SPF Record - Basic Setup (Google)
Setting up SPF to help prevent Spoofing (Microsoft 365)
What is DKIM?
DomianKeys Identified Mail (DKIM) is a way for a mail system to ‘sign’ messages as a form of authentication. It is another way to prevent spoofing by allowing the recipient of an email a way to validate the sender of the email based on the server it originated from.
While SPF lists the IP addresses an email from your domain is allowed to be sent from, DKIM works by 'stamping’ the message with a cryptographic signature to show the mail system it came from. Recipients of the email can check authenticity of the the email by validating the result of the mail servers key and the output of the function equating the ‘stamp’.
While a bit complicated, administrators just have to know that mail systems can use DKIM to validate a message is originating from the server it says it is using cryptography.
To enable DKIM, a step-by-step guide can again be found on both Google and Microsoft’s documentation pages respectively.
Turn on DKIM for your domain (Google)
Use DKIM to validate emails sent from your custom domain (Microsoft 365)
What is DMARC?
Domain-based Message Authentication Reporting and Conformance (DMARC) is a system that looks at the results of checking the SPF and DKIM results of a message. It allows a mail system to process messages that fail one or both methods of authentication and route mail accordingly.
It also gives administrators the flexibility of quarantining or deleting emails that fail SPF and DKIM checks. Admins can also elect to receive updates or alerts when messages fail and are quarantined.
Again, both Google and Microsoft support and offer documentation on adding DMARC to your DNS record:
Add your DMARC record (Google)
Use DMARC to validate email (Microsoft)
Validating DNS Settings
Organizations can use a tool like MxToolbox SuperTool to scan their domain’s DNS settings to confirm DMARC has been configured correctly. In the example below, you can see that google has successfully configured DMARC to quarantine / reject emails based on their SPF / DKIM checks.
The MXToolbox results show DMARC records published and enabled for the google.com domain.
3. Add External Sender Banners
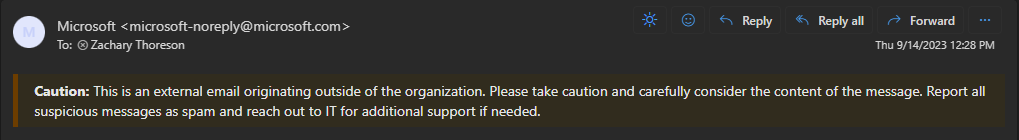
Adding an additional note to e-mails originating from outside of an organization can help improve employee recognition of potential spam and phishing emails. These banners appear at the top of an e-mail and let the recipient know it is from outside of the organization.
In the example below, an email I have received from Microsoft displays the banner:
The banner is attached to urge additional caution when dealing with messages external to the organization.
Thoreson Consulting recommends using an External Sender Banner to add a disclaimer to remind employees not to click on links or provide information unless the email is expected. Additionally, the banner can be customized to remind employees to report spam messages and to reach out to IT support should they require additional help.
Lazy Admin offers an excellent step-by-step blog on how to Configure External Sender Banners for Office365. Google also offers guidance on Configuring External Sender Banners in their Google Workspace Admin Help articles.
4. Build an Inventory
Securing an organization’s assets becomes incredibly challenging if the organization is unsure of the assets it owns. Small and medium organizations should work to build a record of what assets its in possession of and responsible for. This should include physical assets like phones, laptops, and servers but also digital assets such as license keys, software registration, and operating system versions / seats.
Critical components of an asset inventory include both physical and digital assets while denoting assets that may be exposed to the internet or contain sensitive data
Organizations should take note of any assets that can be considered a ‘Crown Jewel’; a collection of assets that are absolutely vital to the organizations continued operations. Crown Jewels are often resources that must remain accessible to customers, contain sensitive data, or are essential to business operations.
Another key area when developing an inventory is making note of any externally facing assets. These assets, such as VPNs, servers, websites, etc. are much more important to keep up to date and secure due to their nature of being exposed to the internet. Its vital organizations are aware of their external asset presence as these are often the windows and doors into the network that attackers try to gain access to first.
Smaller organizations can start small with something like a spreadsheet to keep a running record of assets including their serial numbers, location, who they’re assigned to, and end-of-life dates. However, over time and as an organization grows, it is best practice to leverage a more formal asset management tool. Asset management solutions can scan the organization’s network for devices and collect important information on each asset and even detect the deployment of new assets.
Building an inventory in some capacity is a Quick Win as it does not cost much to get going but can prevent assets from being lost or stolen, help ensure things are up to date, document mission critical assets, and assist in keeping track of an organization’s external footprint.
For more best practices, check out Thoreson Consulting’s blog ‘Building a Cybersecurity Strategy: Asset Management’.
5. Train Your Employees
Research conducted by Stanford University found that 88% of security breaches had some sort of human element involved. Whether human error or a falling victim to a social engineering attack, often times the easiest way into an organization for an attacker is via its employees. The human element is often a blind spot to organizations that spend a heavy amount on new technical controls but neglect employee security awareness training.
It is important to encourage a culture of security awareness within an organization. Emphasize the benefits of getting a second opinion on a suspicious email and reporting phishing emails to the security team. Additionally, investing in security training services to simulate phishing attacks or offer micro trainings can pay dividends in preventing phishing attacks.
While enabling MFA (Quick Win #1) and ensuring email authentication is enabled and configured correctly (Quick Win #2) reduce risk and impact, it is inevitable that employees of an organization encounter a phishing email. Make sure employees within your small business are prepared to face a potential phishing email. You can get started with our ‘How to Gut a Phish [Dissecting a Phishing Email]’ blog post, but more formal training is essential to give employees an edge.
Executives and employees with access to particularly sensitive information such as financial records or intellectual property should undergo training on spear phishing. Attackers will craft phishing emails or social engineering attacks to specifically target key individuals, often leveraging enticing offers for recognition or promotion. For example, an executive may receive an invite to speak at a prestigious conference with a phishing link disguised as a registration link or with malware in a file attachment. It is important key individuals in the organization are exceptionally aware of the dangers online.
Wrapping Up
The 5 ‘Quick Wins’ outlined in this blog article are a great way for small businesses to get started in securing their organization. While it offers a great path forward, it is important to remember security is a constant ongoing process. Organizations can identify all of their weaknesses in a comprehensive Security Risk Assessment and work towards the implementation of a formal Information Security Program (ISP).
There are many technical and administrative challenges organizations must face when looking to improve security and reduce risk, but Thoreson Consulting is here to help. We offer assistance through both our Security Risk Assessment and virtual Information Security Officer (vISO) product offerings.
We hope you have found value in our 5 Easy Steps, but should you have questions or difficult implementing the recommendations, please do not hesitate to reach out to us. We’d be happy to assist your organization and offer guidance on your journey,